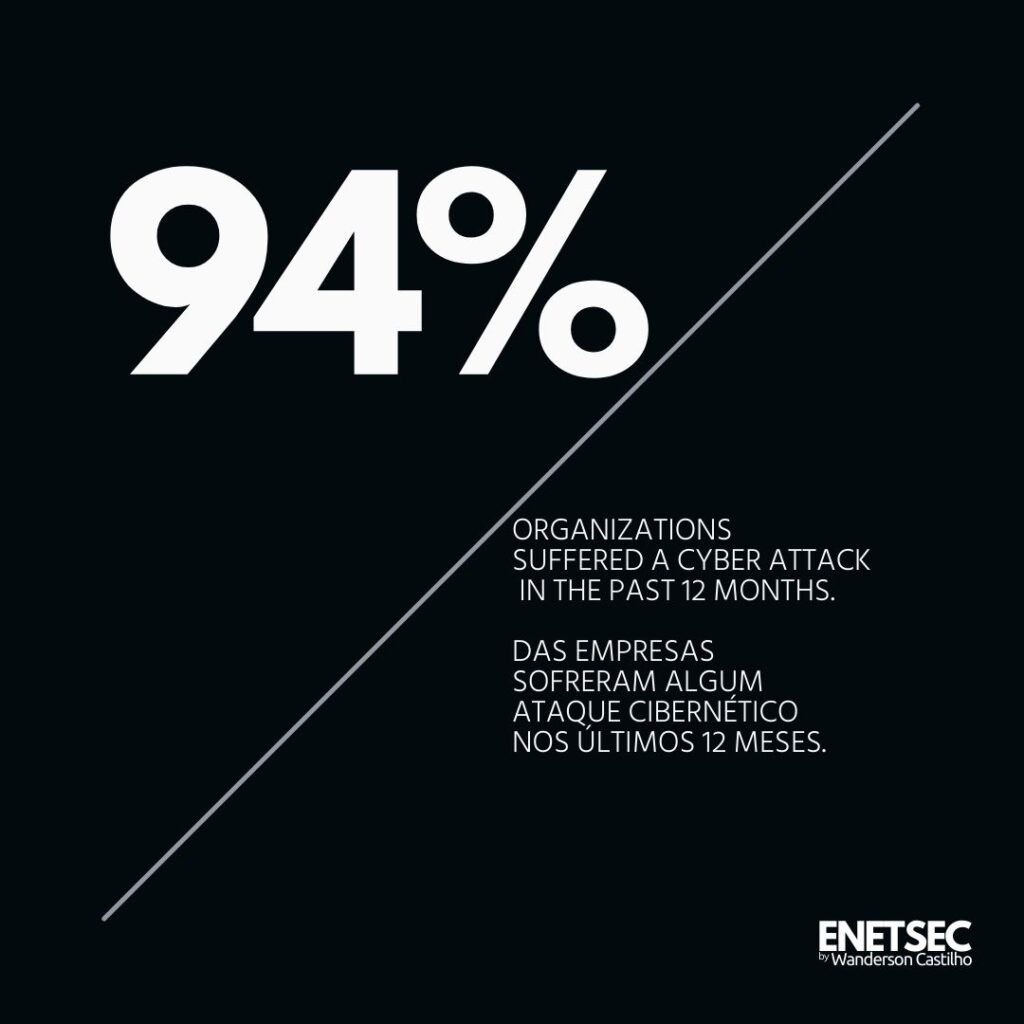
Cybersecurity is the monitoring of protective systems, networks, and programs to prevent digital attacks that aim to access, change, or destroy sensitive information, extort cash from users, or interrupt business practices.
Incident response
Our consultants combine investigative and remediation expertise to assist you with a wide range of issues, from technical response to crisis management.
System audits
Our team of experts are trained to personally audit each system and ensure that they are adequately protected from threats and are working fine.
Penetration test service
Pentest services delve deeper to pinpoint pathways to access, ranking the potential risks and providing a clear roadmap for remediation. Our team of ethical hackers conducts a comprehensive assessment and recommending ways to block attacks before they damage your bottom line.
Types of penetration testing services:
Spyware detection
Spyware can infect any device and give cybercriminals full access to sensitive information such as passwords, banking information, or your entire digital identity. Enetsec identifies, investigates, and responds to cyber threats like these.